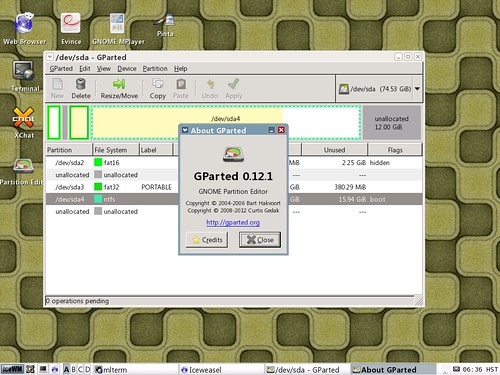
XDM, short for X Display Manager, is my favorite login manager for its simplicity. Sure, gdm and kdm are visually pleasant, but why do I have to install all the dependencies if xdm provides the same functionality as them? After all, xdm can launch GNOME and KDE for you — you just need to fix your ~/.xsession file. This post will serve as my notes on installation, configuration and customization of xdm.
All configuration of xdm, except for distribution-specific settings, is done by modifying the files in the /etc/X11/xdm directory. For now, I'll just go over what I have in my xdm files.
/etc/X11/xdm/Xaccess
This file is used to tell xdm who can use xdm. Therefore, if you are happy to let anyone access the X-Windows desktop locally or remotely, then you would just put an asterisk (*) in Xaccess as I did.
*
If you are very keen on security, you would put only the following in Xaccess. This only allows local users to have access to xdm.
localhost
127.0.0.1
However, even if Xaccess is set up as above, remote xdm login may still be possible with SSH X11 forwarding.
/etc/X11/xdm/Xresources
Xresources file is used to fine-tune the behavior and appearance of XDM. Here is what I put in my Xresources file:
Xcursor.theme: redglass
xlogin*login.translations: #override \
Ctrl<Key>R: abort-display()\n\
<Key>F1: set-session-argument(failsafe) finish-field()\n\
<Key>Delete: delete-character()\n\
<Key>Left: move-backward-character()\n\
<Key>Right: move-forward-character()\n\
<Key>Home: move-to-begining()\n\
<Key>End: move-to-end()\n\
Ctrl<Key>KP_Enter: set-session-argument(failsafe) finish-field()\n\
<Key>KP_Enter: set-session-argument() finish-field()\n\
Ctrl<Key>Return: set-session-argument(failsafe) finish-field()\n\
<Key>Return: set-session-argument() finish-field()
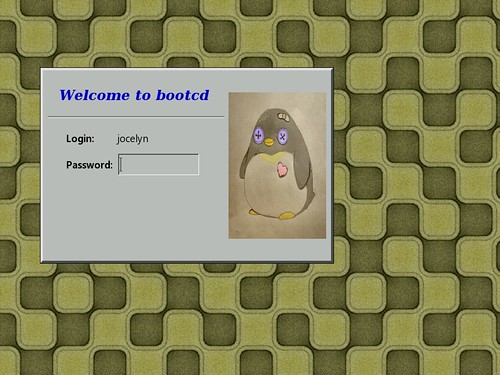
xlogin*greeting: Welcome to CLIENTHOST
xlogin*namePrompt: Login:\040
xlogin*passwdPrompt: Password:\040
xlogin*fail: Login incorrect
xlogin*greetFace: Serif-21:bold:italic
xlogin*face: Sans-15
xlogin*promptFace: Sans-15:bold
xlogin*failFace: Sans-16:bold
xlogin*geometry: 600x400
xlogin*borderWidth: 1
xlogin*frameWidth: 5
xlogin*innerFramesWidth: 2
xlogin*shdColor: grey30
xlogin*hiColor: grey90
xlogin*background: grey
xlogin*greetColor: Blue3
xlogin*failColor: red
*Foreground: black
*Background: #fffff0
xlogin*logoFileName: /usr/share/X11/xdm/pixmaps/penguin_doll_200x300.xpm
xlogin*useShape: true
xlogin*logoPadding: 10
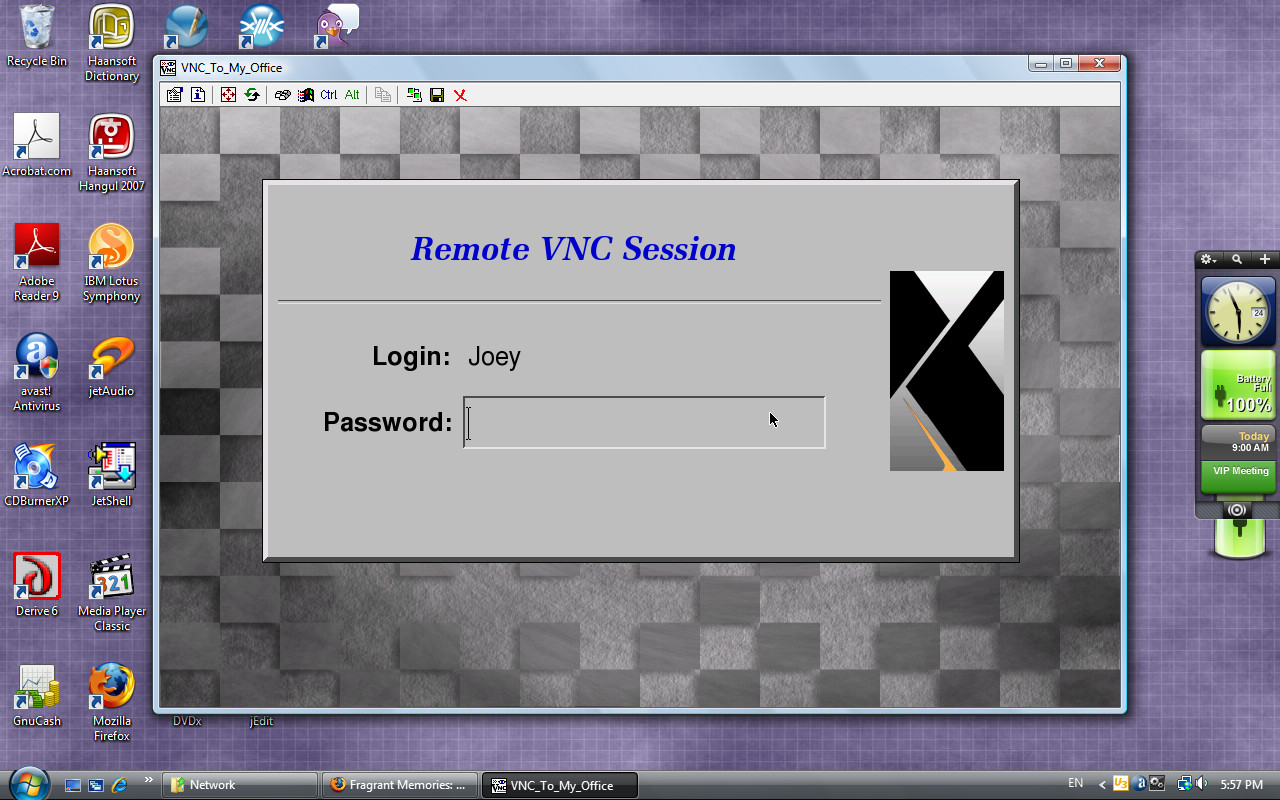
I think the settings are self-explanatory. This is how xdm would look with the above settings. The penguin image was taken from here.
/etc/X11/xdm/Xresources
The Xresources file allows you to specify how many X servers to run and their command arguments. In my case, I run Xorg and Xvfb. Xorg is the standard X server, and Xvfb is a server that runs totally in memory without depending on the video hardware. To see what's going on with Xvfb, I use x11vnc and gvncviewer.
# Default X.org server
:0 local /usr/bin/Xorg :0 vt7 -br -dpi 96 -nolisten TCP
:1 local /usr/local/bin/Xvfb :1 -dpi 96 -screen 0 1024x768x16
/etc/X11/xdm/Xsetup
Xsetup allows you to write any command to run when xdm displays the login screen. In my case, I run gm to set up the background image and run x11vnc to remotely access Xvfb via VNC.
#!/bin/sh
#
# This script is run as root before showing login widget.
gm display -window root /usr/share/wallpapers/Board_Tile_Gray.jpg
xkbcomp -dflts -I/usr/share/X11/xkb /etc/X11/xkb/server-0.xkm $DISPLAY
PID_XVFB=$(pidof Xvfb)
PID_X11VNC=$(pidof x11vnc)
if [ -n "$PID_XVFB" -a -z "$PID_X11VNC" ]; then
x11vnc -display :1 -bg -xkb -nopw -nc_cr -forever -listen localhost -auth $(find /var/lib/xdm/authdir/authfiles -name \*:1\*) > /var/log/x11vnc.log 2>&1
fi
/etc/X11/xdm/xdm-config
In xdm-config, there is only one line that I bother to change. This line enables remote xdm logins.
! SECURITY: do not listen for XDMCP or Chooser requests
! Comment out this line if you want to manage X terminals with xdm
DisplayManager.requestPort: 177
/etc/X11/xdm/xdm-options
I think xdm-options is Debian specific. I don't think I made any change in this file.
# configuration options for xdm
# See xdm.options(5) for an explanation of the available options.
no-ignore-nologin
no-restart-on-upgrade
no-start-on-install
use-sessreg
Resetting XDM
There are other files in /etc/X11/xdm directory that you can safely leave as is. After you make any change with the files, have xdm reread the config files.
kill -1 $(pidof xdm)
If you want to force xdm to kill all running sessions and restart, enter the following command.
/etc/init.d/xdm restart
That's all I have to write about xdm for now. In summary, xdm is a simple, yet functional login manager that is easy to set up.